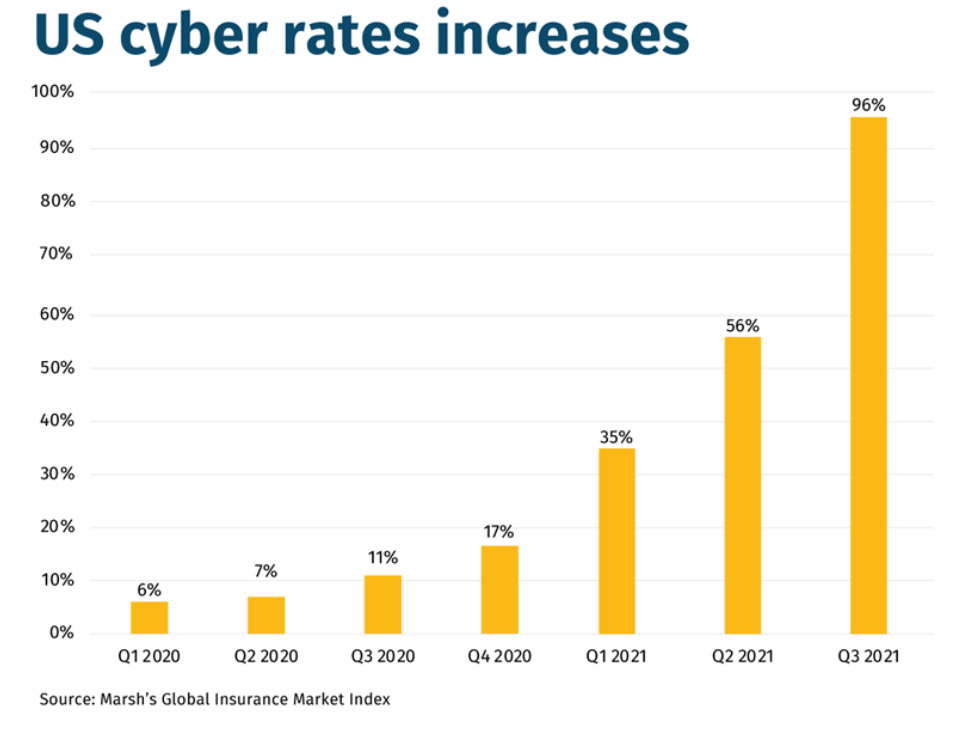
Businesses face major price hikes and reduced liability from their cyber insurance providers in 2022. According to Marsh, the cost of cyber insurance cover grew in the US by 130% in the fourth quarter of 2021, while in the UK it grew by 92%.
Prices will continue to rise as insurers react to increasing numbers of claims: “In the last two years cyber criminality has become a real problem in the corporate world through ransomware…” Observed Adrian Cox, Chief Executive of London-listed Beazley “… insurers are reacting to that and working out how to underwrite it.”.
The 2021 Annual Threat Monitor from NCC Group analysed cybersecurity events that occurred during 2021 and noted that ransomware attacks rose by 92.7% in 2021. The increase in ransomware attacks coincides with the COVID-19 pandemic, with ransomware accounting for 65.4% of all incidents dealt with by NCC global cyber incident response team (CIRT) in 2021. 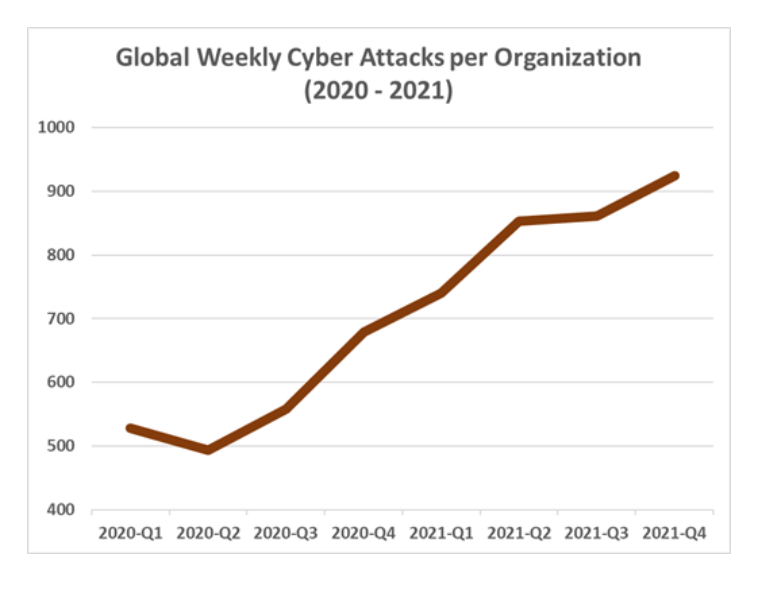
source: https://blog.checkpoint.com
According to IBM’s Cost of a Data Breach 2021 Report, data breach costs rose from USD 3.86 million to USD 4.24 million, the highest average total cost recorded in the history of this report. The insurance market has hardened considerably regarding cyber and technology, on account of Underwriters having seen the number of claims notifications increasing. Cyber insurance claims have grown by around 40% on average in the past four years, while premiums have only grown by half that.
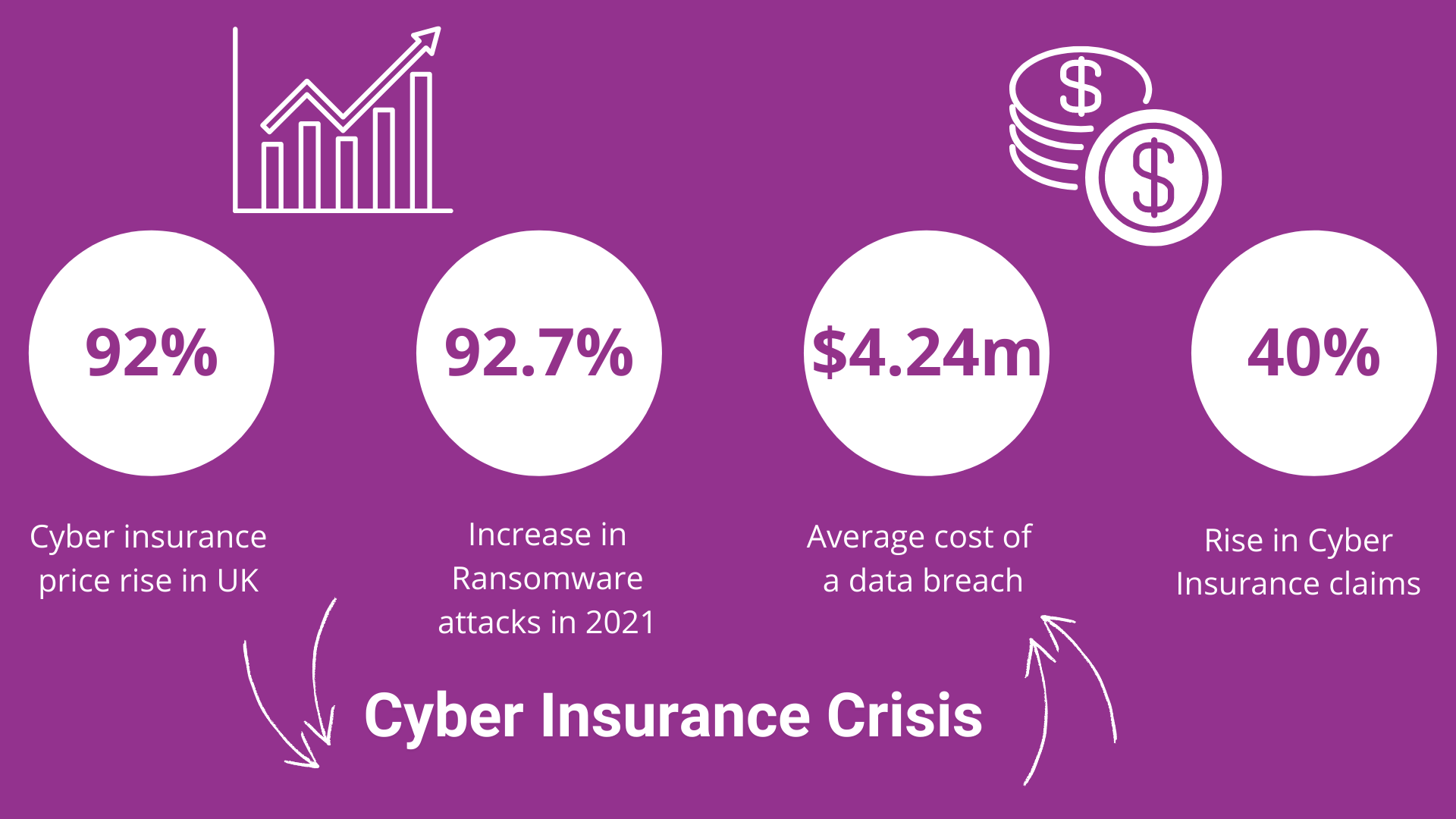
As such, insurers are seeking to reduce their exposure by reducing the amount of capacity that they put down on a given risk. Many cyber and tech limits have been reduced by at least half in recent times and some even further.
Reasons for cyber insurance price hike and liability reductions
Market factors have created a perfect storm of issues which have applied increasing pressure on cyber insurance companies:
- Growing demand for cyber insurance
- Increased ransomware attacks leading to large claims & pay-outs
- Increasing loss ratios for cyber insurers
- Inability to control supply chain partner risk
- Exposure to attack created by work-from-home trend
“Cyber risk has undergone multiple episodes of change and development in its relatively short history, but nothing quite so impactful and fundamental as the events over the last couple of years.” Shay Simkin, Global Head of Cyber at Howden observed, “Covid-19 and all of its attendant effects on technology adoption and cyber security, combined with independent or connected changes to the loss environment, has added a big dose of complexity into an already complicated risk landscape.”
What can you do to control your cyber insurance costs?
Whilst it is not possible to control the broader market pressures that are driving up prices, you can potentially lessen your premium increases by taking cybersecurity seriously. Not only is this good practice but for many insurers some of these recommendations are now becoming mandatory.
Implement ransomware detection and recovery
The best way to significantly reduce potential downtime from a ransomware attack is to prevent your organisation from becoming a victim of an attack in the first place. So, what should you do?
Check out our blog post: Five Tips to combat ransomware
Consider investing in a content management platform that detects ransomware signatures and flags unusual file behaviour like high-volume encryption activity. This technology can also enable you to return to earlier versions of your data, using snapshot recovery. amatis can provide a snapshot recovery service using Veeam – click here for more information. With detection and recovery solutions in place, you reduce the likelihood of potential attacks and recover much more rapidly when attacks bypass your security defences.
Utilise multi-factor authentication
Multi-factor authentication (MFA) is one of the most effective deterrents against cyber-attacks. With MFA, your users need to have two, or more, factors to authenticate their access to your systems, no longer relying solely on basic usernames and passwords. According to Microsoft research, use of MFA is so effective it can block up to 99.99% of automated attacks.
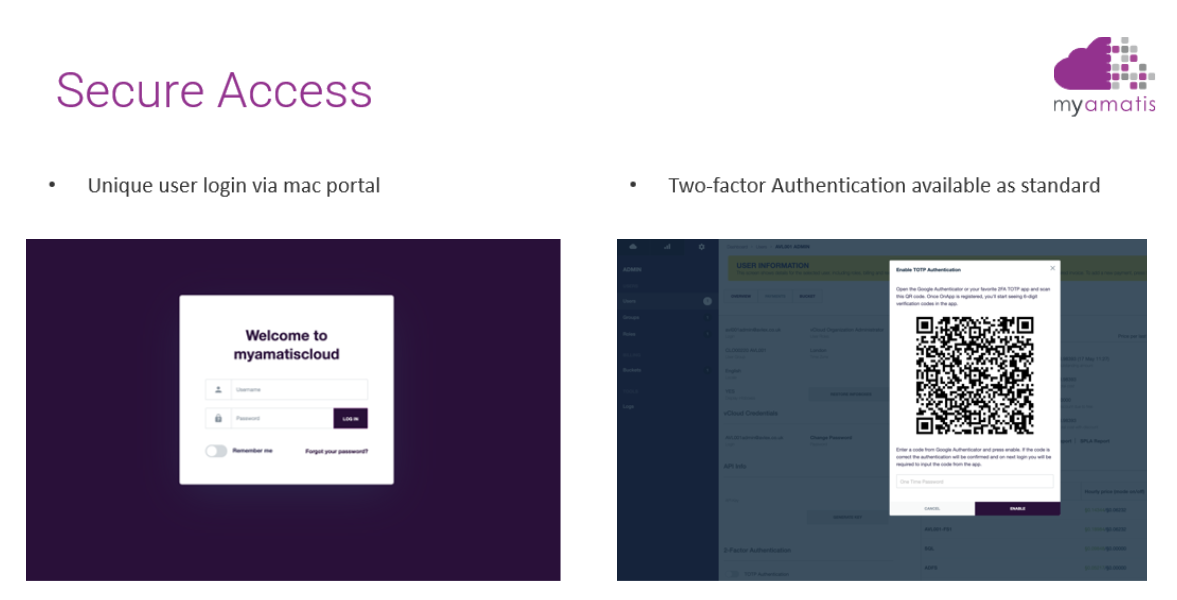
We provide MFA as standard on our myamatis cloud product.
Layer your security protection
Creating a combination of different types of protection adds depth to your security set-up. Use anti-virus protection, coupled with intrusion detection systems, multi-factor authentication and data encryption, coupled with your existing data protection.
Train your users to be risk-aware
Employees should be given cyber security training in order to recognise risks. They should be taught to spot and report any unusual activity, unauthorised file access behaviour, unexpected password or network access alerts or obvious phishing emails. User training will empower employees to make better decisions on an everyday basis.
Develop a thorough and proactive Incident Response Plan
Creating a comprehensive, documented incident response plan is one of the best ways to demonstrate to cyber insurers that you are well prepared. Your plan should include all the security controls you currently have in place and demonstrate how you proactively manage supply chain partner risk. Most importantly, your plan must be routinely reviewed and updated to reflect changes in the technology landscape and data privacy laws.
Use a private network
Network level protection has a key role to play in prevention as malware programs communicate with their operators over the public internet, so restricting incoming and outgoing web traffic can limits the effects of the exploit.
However, only systems underpinned and protected by private network infrastructure can effectively prevent or reduce the potential for attack. By not exposing key infrastructure, applications and services to the public Internet at any point and leveraging the benefits of private cloud for specific mission critical and bespoke applications you can reduce the risk of attack.
Where public cloud environments are already in place or required, there is also the flexibility to engineer hybrid cloud environments. These utilise private interconnects to integrate public and private clouds, creating seamless and responsive end-to-end solutions. Such an approach provides inherent layers of risk reduction against attack with multiple routes in/out of cloud environments, as a well as ensuring data traffic remains away from the public Internet.
Conclusion
Price hikes and reduced coverage are inevitable as Cyber Insurance companies weather the perfect storm so all businesses really do to survive is take precautionary steps to make sure they are prepared for the worst.
“Claims are up, capacity is down and underwriting profitability is, at best, under pressure. The impact on insurance buyers is stark – the importance of being prepared for a cyber-attack has never been clearer.” Shay Simkin, Global Head of Cyber at Howden, concludes. “With insurers now demanding markedly higher cyber security standards before deploying capacity, businesses need analytical solutions designed specifically for them, combined with focused, expert intermediation to help them secure the coverage that meets their needs.”
Find out how amatis Networks can help your business mitigate the potential impacts of cyber-attacks by leveraging our resilient, secure private networks and private/hybrid cloud infrastructure – hosted in our own secure colocation data centres with fully managed services available including 24/7 network monitoring and onsite technical support.