In honour of the annual Shark Week, which takes place every year in July or August, the last blog in our cyber attack blog series, dives into the shark-infested waters of Phishing.
What is Phishing?
Simply put, phishing is a social engineering attack (a range of malicious activities carried out through human interaction) whereby cyber criminals trick their victims into handing over sensitive information through; what appears to be, a genuine method of digital communication from a trusted sender.
Note how genuine this email from PayPal appears. However, upon closer inspection, you can see the email address says otherwise.
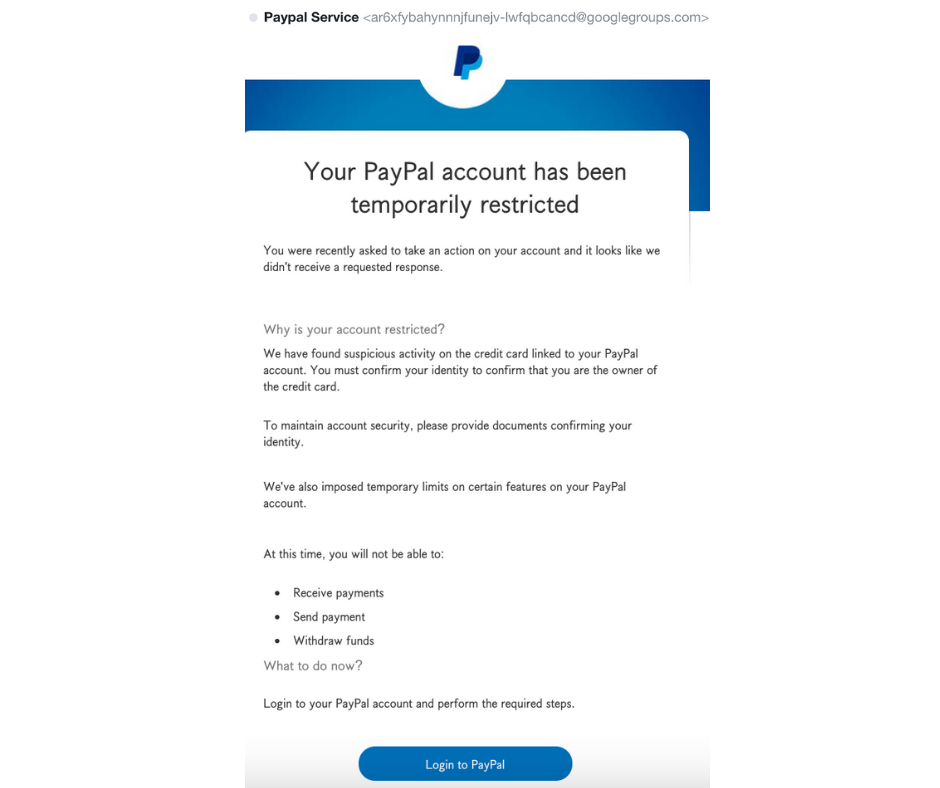
Most phishing attempts use two methods as bait. A malicious attachment or a link (as per the above example) to a malicious website.
Catch of the day
A recent 2021 report from Cisco found that 86% of organisations had at least one user try to connect to a phishing site.
Another recent study found 60% of organisations considered data loss to be a consequence of a phishing attempt.
As lockdown started to draw to an end, tickets for UK attractions skyrocketed. Action Fraud noted that over £1million has been lost to ticket fraud this year alone, with an average loss of £850 per victim
What lurks beneath the water?
These are some of the red flags you need to be aware of in a typical phishing email:
Sender
- Check the email address. Some email addresses such as the PayPal example above, are quite clearly out of sorts
- If you are not familiar with the sender, advice is to tread carefully
- Ensure that the domain is one that, the sender would use.
To
- If the email was sent to a group of people, do you recognise any of the other email addresses?
Hyperlinks
- Never click on a hyperlink if you are at all unsure
- Examine all hyperlinks by hovering over the link; Does the URL look fishy? Is it unrelated to the topic within the method of communication? Is the website it is linking to misspelt?
Subject line
- Is the subject line relevant to the content?
- Is the wording misspelt?
Attachments
- As with a hyperlink, never click on an attachment if you are at all unsure
- Is the attachment reference relevant to the content?
- Were you expecting an attachment from the sender?
- Is it out of character to the sender, to include an attachment?
Content
- Are you being coaxed into clicking on a link or opening an attachment to avoid a negative impact? Do not be fooled!
- Is the content out of the ordinary?
- Are there spelling and grammatical errors?
- Does the content make you feel uncomfortable or uneasy?
Tools in the tackle box
Now we know the warning signs, what tools should you keep in your tackle box to avoid a phishing attack?
- Make it difficult for attackers to contact your employees
- By implementing anti spoofing controls
- Assessing what information is available on your website and social platforms
- Consider a filtering and blocking service – Protective DNS (PDNS)
- Train staff on cyber security and help them recognise fraudulent requests
- Protect your organisation
- Two Factor Authentication (2FA)
- Consider Password management tools such as 1Password
- Consider alternative log in tools such as biometrics
- Remove or suspend all inactive accounts
- Review your passwords (and password policies. As a good rule of thumb, we recommend at least 8 characters, including an upper- and lower-case letter and at least 1 special character and number
- Respond quickly and efficiently in the event of an attack
- Define an incident response plan
- Report all incidents to the National Cyber Security Centre (NCSC) and the authorities via Action Fraud
In the word of GI Joe: “Knowing is half the battle” and now that we have shared with you some of the main threats in Cyber Security, see how amatis can help elevate your internet security.
Contact us today: +44 (0) 118 321 9944 or email [email protected]
